This is the second in a series of posts exploring What’s New in BizTalk Server 2013 R2.
With the BizTalk Server 2013 R2 release, Microsoft has finally implemented a common request to have some level of built-in monitoring tool for a BizTalk Server installation. While this built-in option won’t replace things like the BizTalk Server 2013 Monitoring Management Pack for System Center Operations Manager, or come remotely close to the feature set of third party options like BizTalk360 or AIMS for BizTalk, but it does provide an out-of-the-box solution for performance monitoring, environment validation and notifications.
Ultimately, this tool was built by the same project team that created the MsgBoxViewer tool (MBV), and represents an effort to more tightly integrate this stand-alone tool with the BizTalk Server Administration Console.
The first release supports the following features, with updates promised in the future:
- Ability to monitor multiple BizTalk Server environments
- MBV report generation and viewing
- Dashboard view for overall BizTalk Server environments health
- Scheduled report collection
- Email notifications
- Performance monitor integration with pre-loaded scenario-based performance counters
- Report management
I Have BizTalk Server 2013 R2, But Where Is This Health Monitor?
Unfortunately, the Health Monitor is not registered for use by default, and doesn’t show up anywhere by default. Before making use of it, you’ll have to do some dirty work to get it prepared for use. The core files live under the BizTalk Server installation directory at SDKUtilitiesSupport ToolsBizTalkHealthMonitor.
So what do we do here? We need to run InstallUtil.exe against the MBVSnapin.dll. In order to accomplish this, we can either drop to the command line, or drag and drop MBVSnapin.dll on InstallUtil.exe.
Once it is registered, you can add it to a Management Console alongside the BizTalk Server Administration Console for an all-up management experience.
In order to do that, run mmc /32

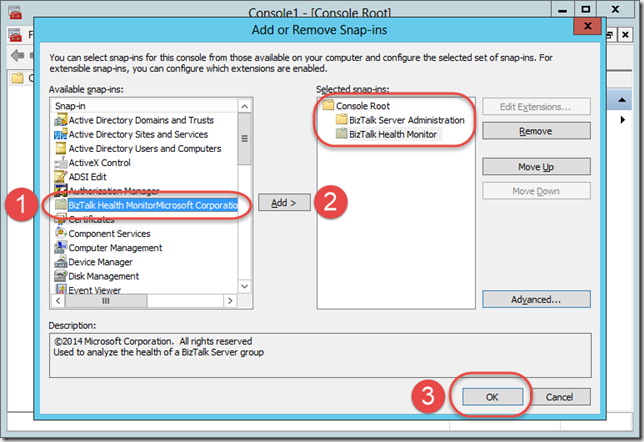
After a nice clean and empty management console appears, press CTRL+M, and then add both the BizTalk Health Monitor and the Microsoft BizTalk Server Administration snap-ins to the console.
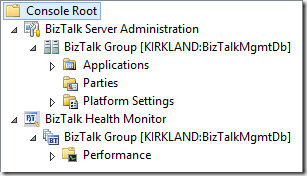
You end up with an Administration Console window containing the items shown in the screenshot below. This might be a good opportunity to add the Event Viewer snap-in for each of your runtime servers as well. At this point, you may want to save the console setup for later use.
What Can I Do with This Thing?
If you expand the Performance node, and click Current Activity, you will be able to examine select performance counters across your BizTalk Server installations through an embedded perfmon display.
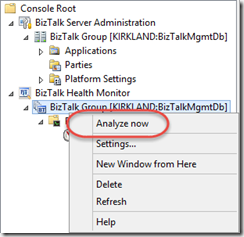
If you right-click each BizTalk Group within the Health Monitor, you have the ability to execute a set of rules that validate your installation while highlighting problem areas.
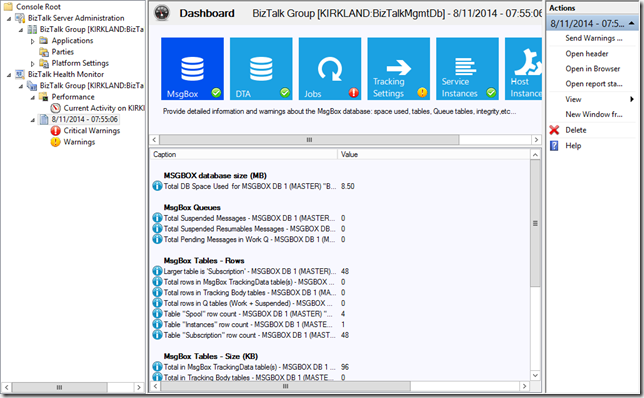
Once you run the analysis, a node is added to the navigation pane labeled with the date and time of the analysis. This report contains the result of executing validation rules at a fixed point in time. This report can be sent via email, or opened in the browser for additional details.
Right now, it’s looking like my installation is throwing a pretty critical warning when it comes to the Jobs category. Let’s see what that might be.
It looks like the Backup BizTalk Server job hasn’t been enabled, and there isn’t any history indicating that this job has ever executed. That’s fairly concerning and problematic. It would be nice if we could have been notified about that in a more proactive manner.
Enabling Automatic Scans / Notifications
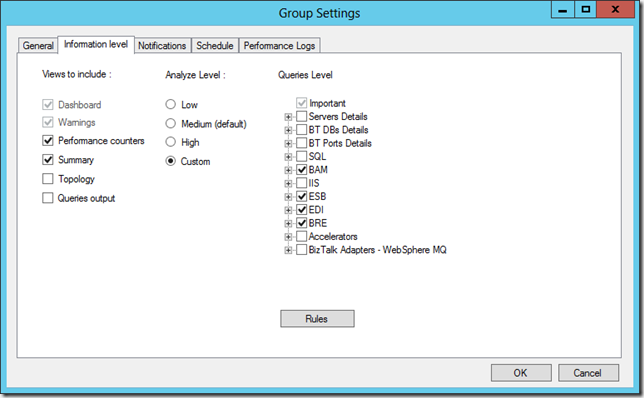
If I go back to the BizTalk Group within the Health Monitor, and click Settings, I will find myself at a screen that enables me to configure automatic analysis of my BizTalk Server Group as well as notifications of scan results.
Additionally, I can even configure the queries executed, rules evaluated, and the views on top of that information I want to include in each analysis.
If I want to enable notifications, I have a few different options. I can either configure email notifications, or if I want to essentially pipe these notifications into another tool that can consume event log entries, I can direct notifications to the event log instead.
More to Come
As mentioned earlier, it sounds like the team is already well underway with an update to this tool, and it’s safe to say that there will likely be more to come. I would venture to guess that this will mean either more features and deeper console integration (since there are still quite a few times where clicking an option launches the browser to show full details). We’ll keep this space updated.
In the meantime, if you’re just now moving to either BizTalk Server 2013, or BizTalk Server 2013 R2, and you want to keep your skills up to date, check out one of our BizTalk 2013 Developer Immersion classes or BizTalk 2013 Administrator Immersion classes. Just this last week, students in the developer class that I taught were able to see this functionality demonstrated live.
If you’re already a QuickLearn student, keep following the blog to get the latest bleeding edge information as it becomes available. The series will continue next week!